Let’s face it—online security is no joke. But hey, who said we can’t have a little fun while we learn? Buckle up, because we’re diving into the world of SSL stripping attacks and how to prevent them on Windows. And yes, there will be humor, because even hackers can’t steal our sense of humor!
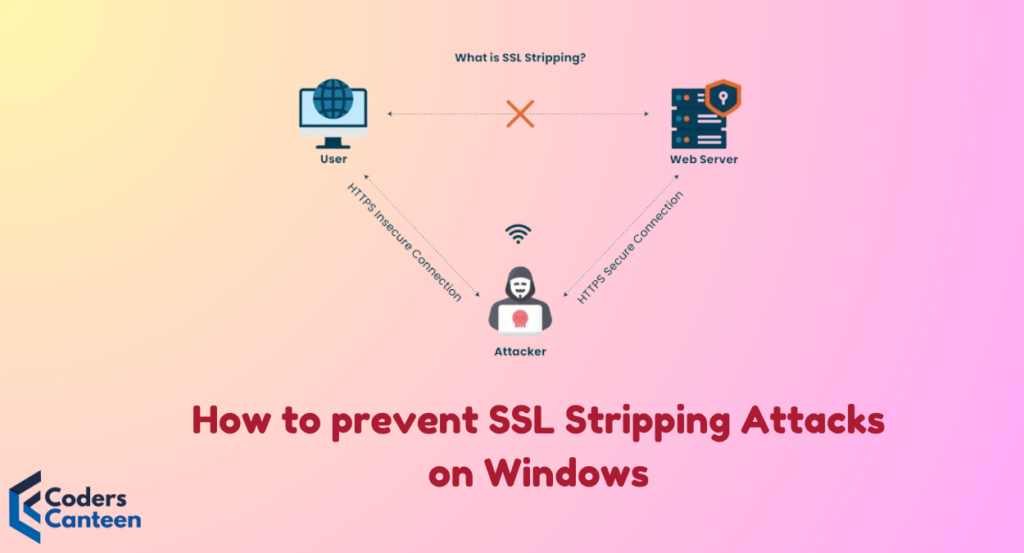
What is SSL Stripping?
SSL stripping, also known as SSL downgrade attack, is like a digital con artist. It’s a technique used by cybercriminals to intercept your secure HTTPS connection and downgrade it to an unsecure HTTP connection. Imagine you’re in a bulletproof car, and suddenly the windows roll down on their own. Not cool, right?
Why Should You Care?
If someone can strip your SSL, they can see everything you’re doing online. Yes, everything—from passwords to credit card numbers. It’s like leaving your diary open in the middle of Times Square. So, unless you want your online secrets out there for the world to see, let’s get into how to stop these sneaky SSL strippers.
Setting Up the Scene
Before we jump into the technicalities, let’s get you in the right mindset. Think of your computer as a medieval castle. SSL is the moat that keeps the invaders at bay. Our goal? To make sure that moat is full and the drawbridge is up.
1. Always Use HTTPS
First things first: Always, and we mean always, use HTTPS. It’s like the golden rule of internet security. When you see “HTTPS” in the URL, it means your connection is encrypted. If it’s just “HTTP”, well, that’s like leaving your front door wide open.
Pro Tip: Use browser extensions like HTTPS Everywhere. This nifty little tool automatically forces your browser to use HTTPS for all websites that support it. It’s like having a guard dog for your internet connection.
2. Implement HSTS (HTTP Strict Transport Security)
HSTS is like that really strict bouncer at the club. It forces browsers to only communicate with your site using HTTPS. No exceptions. Once a site has been accessed with HTTPS, HSTS ensures all future connections use HTTPS as well.
To enable HSTS, you’ll need to add a header to your web server configuration. Here’s how you do it on an Apache server:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"For Nginx, it looks like this:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains";3. Keep Your Software Updated
This might sound obvious, but it’s crucial. Hackers love outdated software the way kids love candy. Updates often contain patches for security vulnerabilities that could be exploited in SSL stripping attacks. So, hit that update button like it owes you money.
4. Use Strong SSL/TLS Certificates
Just like you wouldn’t trust a flimsy lock on your front door, don’t trust weak SSL/TLS certificates. Go for strong encryption with 2048-bit keys or higher. If your SSL certificate is weak, it’s easier for attackers to strip it away.
5. Disable HTTP Access Completely
If your website is HTTPS-only, you don’t need HTTP access. Disabling HTTP can be a bit like getting rid of the wimpy bodyguards and hiring The Rock instead. Here’s how you can do it on an Apache server:
<VirtualHost *:80>
ServerName yoursite.com
Redirect permanent / https://yoursite.com/
</VirtualHost>For Nginx:
server {
listen 80;
server_name yoursite.com;
return 301 https://$server_name$request_uri;
}6. Monitor Your Network
Use network monitoring tools to keep an eye on your traffic. Think of it as having CCTV cameras in your castle. Tools like Wireshark can help you detect unusual activity that might indicate an SSL stripping attack.
7. Educate Your Users
Sometimes, the best defense is a good offense. Educate your users about the importance of HTTPS and how to recognize when they’re on a secure site. After all, a well-informed user is less likely to fall for an attack.
8. Use Secure Browsers
Not all browsers are created equal. Some are more secure than others. Encourage your users to use browsers known for their strong security features, like Google Chrome or Mozilla Firefox. They often have built-in protections against SSL stripping.
A Funny Interlude
Ever heard the one about the hacker who walked into a bar? He tried to crack the Wi-Fi password but ended up with just an ‘access denied’ cocktail. Remember, even in the digital world, it’s always happy hour for security!
Advanced Techniques
For those of you who like to live on the edge (in a secure way), here are some advanced techniques to further protect against SSL stripping:
9. DNSSEC (Domain Name System Security Extensions)
DNSSEC adds a layer of security to your DNS queries. It’s like putting a guard at every entrance of your castle. It ensures that the information sent back to your browser from the DNS server is signed and verified, preventing attackers from hijacking your DNS queries.
10. Public Key Pinning
Public key pinning is like a VIP list for your website. It tells browsers which public keys are allowed for your site. If a browser encounters a different key, it throws up a red flag. Here’s an example of how you might implement it:
Header always set Public-Key-Pins "pin-sha256=\"base64+primary==\"; pin-sha256=\"base64+backup==\"; max-age=5184000; includeSubDomains"FAQs
Q: What’s the difference between HTTP and HTTPS?
A: HTTP stands for HyperText Transfer Protocol, while HTTPS is the secure version of it, standing for HyperText Transfer Protocol Secure. HTTPS encrypts the data sent between your browser and the server, making it harder for attackers to intercept.
Q: Can I use free SSL certificates?
A: Yes, free SSL certificates from providers like Let’s Encrypt are perfectly fine for most uses. They provide the same level of encryption as paid certificates, but without the cost.
Q: What should I do if I suspect an SSL stripping attack?
A: If you suspect an SSL stripping attack, disconnect from the network immediately and check your security settings. Use tools like Wireshark to analyze your network traffic and look for suspicious activity.
Q: Are there any tools to help me prevent SSL stripping attacks?
A: Absolutely! Tools like HTTPS Everywhere, SSL Labs, and Wireshark can help you secure your connections and monitor for potential attacks.
Conclusion
Preventing SSL stripping attacks on Windows involves a mix of basic security practices and advanced techniques. By ensuring that HTTPS is always used, implementing HSTS, keeping software updated, and using strong SSL/TLS certificates, you can significantly reduce the risk of these attacks. Remember to educate your users and use secure browsers, and consider advanced methods like DNSSEC and public key pinning for added protection. Keep your castle secure, and don’t forget to have a laugh along the way. After all, security doesn’t have to be dull!